I am using Wordfence security service for a long time now and I was never disappointed.
Their expertise seams genuinely and highly professional but this time I want to mention about an article they shared publicly on their website.
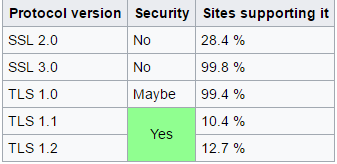
This thread is also a "take that! and inform yourself better" for some, who believe that using a SSL certificate make the site/service bulletproof .
Wordfence posted two articles about HTTPS, the first one is talking about how the encrypted connection is decrypted in order to become "readable" (so SSL becomes useless) and the second article which makes me a bit confused is also posted on their website
Is SSL (HTTPS) useful and secure? - Yes , only when direct visitor-website connection is established
Is SSL certificate delivering a HTTPS connection bulletproof? - Nope if a 3rd party service/function must decrypt the connection in order to read data... The next logic question is... Can be exploit with malicious intent? Yup.
Their expertise seams genuinely and highly professional but this time I want to mention about an article they shared publicly on their website.
This thread is also a "take that! and inform yourself better" for some, who believe that using a SSL certificate make the site/service bulletproof .
Wordfence posted two articles about HTTPS, the first one is talking about how the encrypted connection is decrypted in order to become "readable" (so SSL becomes useless) and the second article which makes me a bit confused is also posted on their website
This morning we are publishing a public service post showing how malicious phishing sites are getting valid SSL certificates from certificate authorities. In Chrome, this means that a phishing site is labeled as 'Secure'.
We also show that even if a certificate authority realizes they issued a certificate to a malicious site, when they revoke that certificate, Chrome still shows the site as 'Secure'. The fact that the certificate is revoked is buried deep in Chrome developer tools where most people won't find it.
We think this is something every online user should know about and we explain how to protect yourself and your friends and family against the large number of phishing sites that are now installing free valid SSL certificates and are shown as 'Secure' by Chrome.
You can find the full post on our blog....
Is SSL (HTTPS) useful and secure? - Yes , only when direct visitor-website connection is established
Is SSL certificate delivering a HTTPS connection bulletproof? - Nope if a 3rd party service/function must decrypt the connection in order to read data... The next logic question is... Can be exploit with malicious intent? Yup.