As a premium user of mfc for many years, some things really suck at their website.
OK, there are many, many websites about camgirls out there, but here mfc is the topic.
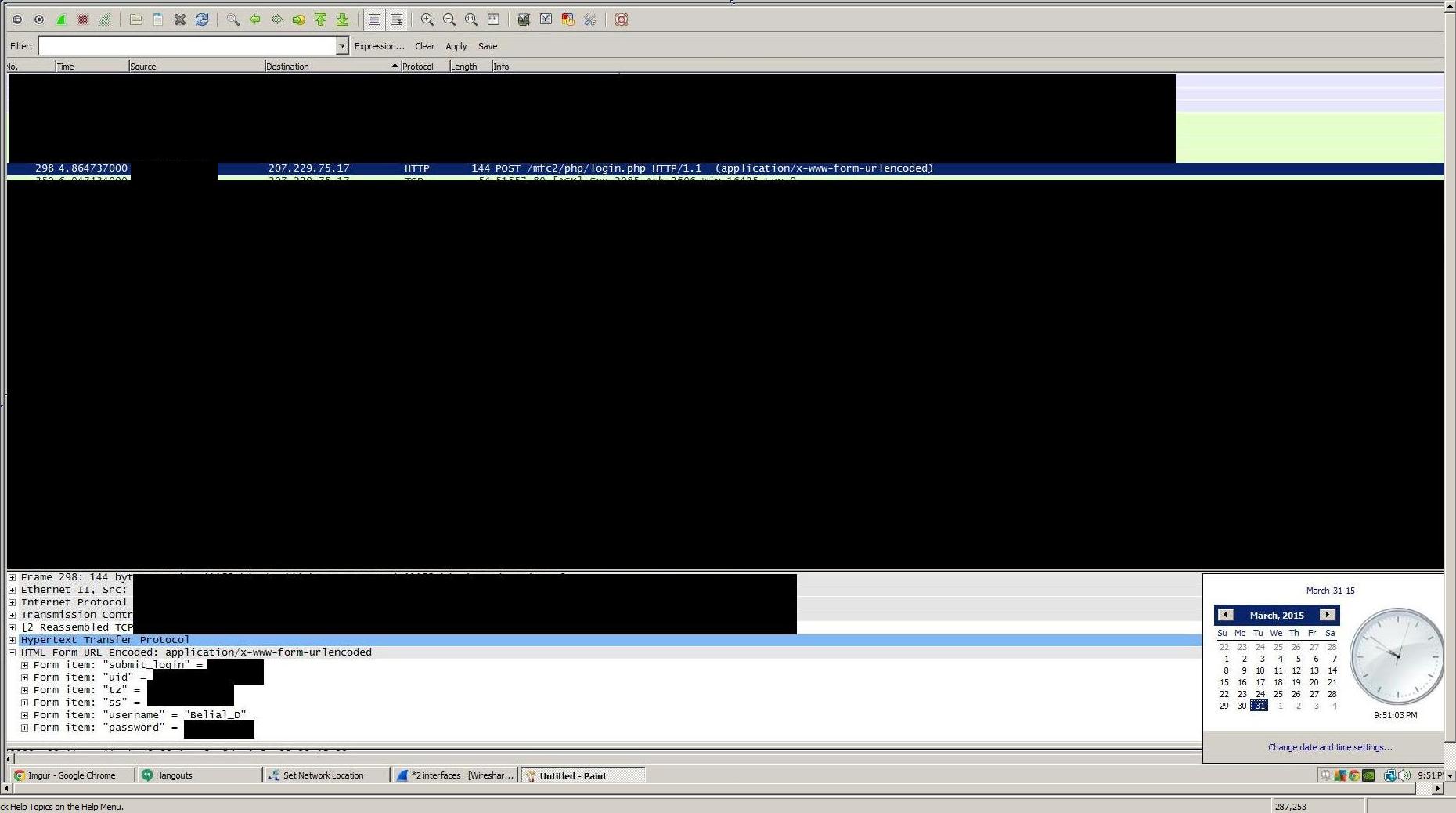
I’m not a programmer nor a security expert, but looks like they have to do a lot of work.
Thats why i post here some thoughts about what’s wrong with mfc in my opinion.
http://mfcsucks.hol.es
#mfcsucks
OK, there are many, many websites about camgirls out there, but here mfc is the topic.
I’m not a programmer nor a security expert, but looks like they have to do a lot of work.
Thats why i post here some thoughts about what’s wrong with mfc in my opinion.
http://mfcsucks.hol.es
#mfcsucks