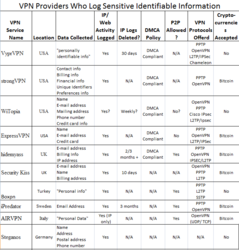
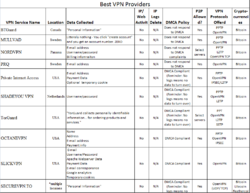
I am in the market to install a VPN onto my computer. Which ones do you use, and why? Which are the best, and worse in your opinion? I want something that will hide my IP, not leave a trail of any sort (back to where I am) and not completely slow down my computer. There are so many different things that are said online about different VPNs, that I don't know where to start.
AmberCutie's Forum
An adult community for cam models and members to discuss all the things!
Which VPN do you use, and why?
- Thread starter noob101
- Start date
-
** WARNING - ACF CONTAINS ADULT CONTENT **Only persons aged 18 or over may read or post to the forums, without regard to whether an adult actually owns the registration or parental/guardian permission. AmberCutie's Forum (ACF) is for use by adults only and contains adult content. By continuing to use this site you are confirming that you are at least 18 years of age.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
If you use the search feature you'll see i've recommended this one several times for a couple years now. So I'll just link to their post.noob101 said:I am in the market to install a VPN onto my computer. Which ones do you use, and why? Which are the best, and worse in your opinion? I want something that will hide my IP, not leave a trail of any sort (back to where I am) and not completely slow down my computer. There are so many different things that are said online about different VPNs, that I don't know where to start.
https://www.ambercutie.com/forums/v...&p=360929&hilit=privateinternetaccess#p359462
Why? Serious question, as I wonder what you think the owner of a site that you connect to can do with your IP address, aside from block it - and even that will be of limited value if using most domestic ISPs as they assign IP addresses dynamically on connection.noob101 said:I want something that will hide my IP, not leave a trail of any sort (back to where I am) and not completely slow down my computer.
I can see the value in bypassing IP geolocation blocks, but struggle after that.
You're sort of asking the wrong question. It's not the owner of the site that is really the concern. Most average websites do nothing with the information. You're right there. And sites where you do business with, amazon, newegg, ebay... they all have your information supplied to them by you.penfold_43 said:Why? Serious question, as I wonder what you think the owner of a site that you connect to can do with your IP address, aside from block it - and even that will be of limited value if using most domestic ISPs as they assign IP addresses dynamically on connection.noob101 said:I want something that will hide my IP, not leave a trail of any sort (back to where I am) and not completely slow down my computer.
I can see the value in bypassing IP geolocation blocks, but struggle after that.
A vpn is primarily to prevent prying eyes from finding out what you are doing and tracking your activities over the entire internet as a whole. This doesn't mean illegal, although it can. It means you simply don't want anyone knowing what you're doing on the internet. Because put simply, it's none of their business and they have no right to know. If you disagree with that then a vpn probably isn't something you'll ever want to look into.
The other big issue is public open wifi spots. You know when you go to McDonalds or Panerra bread to get on their wifi? Everything you do is being broadcast in the clear. People with simple easily attained software can see everything you do. That email you just sent, they read it. They can also intercept cookies and install them on their computers. A vpn encrypts all that, even at public wifi's so nothing can be intercepted.
Basically an unsecured connection means someone is reading everything you do. Could be your isp, could be the courts asking some server company to turn over all their information pertaining to your ip address, could be the guy eating the big mac in the next booth over, or it could just be the NSA (don't delude yourself, they are reading this right now).
For $40 a year it's rather silly and naive not to have one in this day and age.
To put it in different words, this is from this site (click here if you want to read it all)
Why You Need a VPN, or How You Can Benefit from Using One
A VPN alone is just a way to bolster your security and access resources on a network you're not physically connected to. What you choose to do with a VPN is a different story. Usually, VPN users fall into a few separate categories:
The student/worker. This person has responsibilities to attend to, and uses a VPN provided by their school or company to access resources on their network when they're at home or traveling. In most cases, this person already has a free VPN service provided to them, so they're not exactly shopping around. Also, if they're worried about security, they can always fire up their VPN when using airport or cafe WI-Fi to ensure no one's snooping on their connection.
The downloader. Whether they're downloading legally or illegally, this person doesn't want on some company's witch-hunt list just because they have a torrenting app installed on their computer. VPNs are the only way to stay safe when using something like BitTorrent—everything else is just a false sense of security. Better safe than trying to defend yourself in court or paying a massive fine for something you may or may not have even done, right?
The privacy minded and security advocate. Whether they're a in a strictly monitored environment or a completely free and open one, this person uses VPN services to keep their communications secure and encrypted and away from prying eyes whether they're at home or abroad. To them, unsecured connections mean someone's reading what you say.
The globetrotter. This person wants to watch the Olympics live as they happen, without dealing with their crummy local networks. They want to check out their favorite TV shows as they air instead of waiting for translations or re-broadcasts (or watch the versions aired in other countries,) listen to location-restricted streaming internet radio, or want to use a new web service or application that looks great but for some reason is limited to a specific country or region.
Some combination of the above. Odds are, even if you're not one of these people more often than not, you're some mix of them depending on what you're doing. In all of these cases, a VPN service can be helpful, whether it's just a matter of protecting yourself when you're out and about, whether you handle sensitive data for your job and don't want to get fired, or you're just covering your own ass from the MPAA.
Even if none of the above really sound right to you, you can still benefit from using a VPN. You should definitely use one when you travel or work on an untrusted network (read: a network you don't own, manage, or trust who manages.) That means opening your laptop at the coffee shop and logging in to Facebook or using your phone's Wi-Fi to check your email at the airport can all potentially put you at risk.
JerryBoBerry said:The other big issue is public open wifi spots. You know when you go to McDonalds or Panerra bread to get on their wifi? Everything you do is being broadcast in the clear. People with simple easily attained software can see everything you do. That email you just sent, they read it. They can also intercept cookies and install them on their computers. A vpn encrypts all that, even at public wifi's so nothing can be intercepted.
The 'anyone can read it' is true only if you access sites/email over unencrypted protocols (http/imap/pop3); now, if you configured your stuff correctly and prefer secure protocols (https/imaps/pop3s), it's way safer ( MITM attacks are still possible, but there's ways around that like certificate pining.. And MITM attacks are way more complex to pull off correctly). Hopefully HTTP 2.0 will come out soon with its mandatory encryption.
Basically an unsecured connection means someone is reading everything you do. Could be your isp, could be the courts asking some server company to turn over all their information pertaining to your ip address, could be the guy eating the big mac in the next booth over, or it could just be the NSA (don't delude yourself, they are reading this right now).
s/everything you do/everything you do over insecure protocols/
And a VPN just removes the occasional script kiddie/hacker from the equation, but not the state-sponsored attacks/investigations: all it takes is one CALEA request or a court subpoena and any company (including your VPN provider) *will* turn over any logs they have to law enforcement (and even if they claim they don't have logs - that is unlikely to be a reality for long: once they get hit with the first request and get in real trouble for that, they either close down or adequate to following the law).
Now, with that said, I do have (multiple) VPNs that I run myself both to bridge together all the networks I maintain for ease of maintenance as well as encrypting my insecure communications when using public networks and ensuring it goes out from a location I trust (my home or my servers) - if it gets snooped from there, well, it's beyond my control. A side effect as well - sometimes a VPN helps with performance over horrible connections - some companies do traffic shaping/limiting of HTTP traffic.. But they don't touch UDP .
And that's why it's very important to do research first and find out if your VPN keeps records. Not all VPN's are equal. The ones that keep records are worthless. If they don't, there's nothing to turn over when they get the court subpoenas. Privateinternetaccess, the one I mentioned many times before, does not. So there's no records to turn over.weirdbr said:And a VPN just removes the occasional script kiddie/hacker from the equation, but not the state-sponsored attacks/investigations: all it takes is one CALEA request or a court subpoena and any company (including your VPN provider) *will* turn over any logs they have to law enforcement (and even if they claim they don't have logs - that is unlikely to be a reality for long: once they get hit with the first request and get in real trouble for that, they either close down or adequate to following the law).
Also if i remember correctly, Privateinternetaccess uses a shared IP address system. So you're using the same one as several other people with no way to differentiate who requested what. A further layer of security there.
PrivateInternetAccess.com implements an automated virtual private network (“VPN”) service. Our service is fully automated and we do not log our user’s activities. We do not in any way select the recipients our users transmit to or the material our users access while using our service. We do not store, access, or modify any content that our users access while using our service.
As a result, PrivateInternetAccess.com’s VPN service qualifies as a provider of transitory digital network communications under 17 U.S.C. § 512(a) of the Copyright Act. As we do not store any content accessed by our users, we are unable to delete any such content that may be infringing. Because we do not log our users’ activities in order to protect and respect their privacy, we are unable to identify particular users that may be infringing the lawful copyrights of others.
http://www.deepdotweb.com/2014/07/08/is-your-vpn-legit-or-shit/
Mullvad for instance is another excellent choice. Swedish, no records, no email address. Click subscribe and they give you an account number. Can pay with bitcoin or cash (and other methods). Mail cash and there's literally no trace whatsoever to you. Court subpoena's are useless.
Attachments
JerryBoBerry said:And that's why it's very important to do research first and find out if your VPN keeps records. Not all VPN's are equal. The ones that keep records are worthless. If they don't, there's nothing to turn over when they get the court subpoenas. Privateinternetaccess, the one I mentioned many times before, does not. So there's no records to turn over.
Until the first interesting case involving them happens and they suddenly find themselves in the crosshairs of all three-letter agencies, law enforcement and regulatory agencies.
As a result, PrivateInternetAccess.com’s VPN service qualifies as a provider of transitory digital network communications under 17 U.S.C. § 512(a) of the Copyright Act. As we do not store any content accessed by our users, we are unable to delete any such content that may be infringing. Because we do not log our users’ activities in order to protect and respect their privacy, we are unable to identify particular users that may be infringing the lawful copyrights of others.
I like how they use copyright law when that's not the section that covers what they do.
Mullvad for instance is another excellent choice. Swedish, no records, no email address. Click subscribe and they give you an account number. Can pay with bitcoin or cash (and other methods). Mail cash and there's literally no trace whatsoever to you. Court subpoena's are useless.
Which means, they are in direct violation of the EU's data retention directive and as soon as they get in any legal threat, their lawyers will tell them to start speaking and get a better deal than a very large civil and criminal suit.
Here's the deal - the internet was *never* designed for anonymity and will never be truly anonymous; any attempts to claim it is possible are by people who have no idea of the regulations that need to be followed (and as such are breaking the law) or who never studied the tech closely. Even something like TOR has been shown to be non-anonymous given the right amount of investment, which is not far from the reach of governments.
Nah, you wouldn't access anything sensitive over a public wifi using a connection that wasn't secured using TLS. Well, I wouldn't. You don't need a VPN to do achieve that.JerryBoBerry said:The other big issue is public open wifi spots.
With regard to tracking, the websites I visit and my browser history are pretty much in agreement. MFC is at the top, which is how come I read this forum. While I don't generally tell people I like to watch women undress in cafes (can thank an ex-girlfriend for introducing me to that particular kink :-D ) and to encourage their daring with tokens, I don't consider it such a great secret that requires me to pay a third party to try to hide the fact.
I am very anti state monitoring of communications without a court order and believe the juristiction where I live has some of the most iniquitous laws in this regard (I financially support a campaigning organisation that includes opposing this in its remit). The only reason I can find for me using one personally is that I think the state needs to learn that if it keeps trying to monitor its citizens, its citizens will take steps to prevent this and that it and its intelligence agencies will have to deal with the fact that they will learn nothing from such monitoring. However, I'd rather use the money it would cost me to do this instead to support campaigns aimed at changing the law.
penfold_43 said:Nah, you wouldn't access anything sensitive over a public wifi using a connection that wasn't secured using TLS. Well, I wouldn't. You don't need a VPN to do achieve that.JerryBoBerry said:The other big issue is public open wifi spots.
People do sensitive stuff like that all the time over a public wifi. For many people it's their only way to get on the internet, or they're travelling. My local McDonalds always has people sitting there for hours (at all hours of the night as well) sipping a $1 soda and using their laptops. A public wifi is one of the best examples where a VPN is needed.
http://www.howtogeek.com/178696/why...erous-even-when-accessing-encrypted-websites/
“Don’t do your online banking or anything sensitive on a public Wi-Fi network.” The advice is out there, but why can using a public Wi-Fi network actually be dangerous? And wouldn’t online banking be secure, as it’s encrypted?
There are a few big problems with using a public Wi-Fi network. The open nature of the network allows for snooping, the network could be full of compromised machines, or — most worryingly — the hotspot itself could be malicious.
Snooping
Encryption normally helps protect your network traffic from prying eyes. For example, even if your neighbor at home is within range of your Wi-Fi network, they can’t see the web pages you’re viewing. This wireless traffic is encrypted between your laptop, tablet, or smartphone and your wireless router. It’s encrypted with your Wi-Fi passphrase.
When you connect to an open Wi-Fi network like one at a coffee shop or airport, the network is generally unencrypted — you can tell because you don’t have to enter a passphrase when connecting. Your unencrypted network traffic is then clearly visible to everyone in range. People can see what unencrypted web pages you’re visiting, what you’re typing into unencrypted web forms, and even see which encrypted websites you’re connected to — so if you’re connected to your bank’s website, they’d know it, although they wouldn’t know what you were doing.
This was illustrated most sensationally with Firesheep, an easy-to-use tool that allows people sitting in coffee shops or on other open Wi-Fi networks to snoop on other people’s browsing sessions and hijack them. More advanced tools like Wireshark could also be used to capture and analyze traffic.
Protecting Yourself: If you’re accessing something sensitive on public Wi-Fi, try to do it on an encrypted website. The HTTPS Everywhere browser extension can help with this by redirecting you to encrypted pages when available. If you frequently browse on public Wi-Fi, you may want to pay for a VPN and browse through it when on public Wi-Fi. Anyone in the local area will only be able to see that you’re connected to the VPN, not what you’re doing on it.
Compromised Devices
Keep Your Windows Computer Secure on Public Wireless Hotspots
If you have a Netbook or Laptop that you would like to use on a Public Wi-Fi hotspot, there are security precautions you need to take. Here we look at keeping your computer secure at public Wi-Fi hotspots. [Read Article]
Compromised laptops and other devices may also be connected to the local network. When connecting, be sure to select the “Public network” Wi-Fi option in Windows and not the Home network or Work network options. The Public network option locks down the connection, ensuring Windows isn’t sharing any files or other sensitive data with the machines on the local network.
It’s also important to be up-to-date on security patches and use a firewall like the one built into Windows. Any compromised laptops on the local network could try to infect you.
Protecting Yourself: Select the Public network option when connecting to public Wi-Fi, keep your computer up to date, and leave a firewall enabled.
Malicious Hotspots
Most dangerously, the hotspot you connect to itself may be malicious. This may be because the business’s hotspot was infected, but it may also be because you’re connected to a honeypot network. For example, if you connect to “Public Wi-Fi” in a public place, you can’t be entirely sure that the network is actually a legitimate public Wi-FI network and not one set up by an attacker in an attempt to trick people into connecting.
Is it safe to log into your bank’s website on public Wi-Fi? The question is more complicated than it appears. In theory, it should be safe because the encryption ensures you’re actually connected to your bank’s website and no one can eavesdrop.
In practice, there are a variety of attacks that can be performed against you if you were to connect to your bank’s website on public Wi-Fi. For example, sslstrip can transparently hijack HTTP connections. When the site redirects to HTTPS, the software can convert those links to use a “look-alike HTTP link” or “homograph-similar HTTPS link” — in other words, a domain name that looks identical to the actual domain name, but which actually uses different special characters. This can happen transparently, allowing a malicious Wi-Fi hotspot to perform a man-in-the-middle attack and intercept secure banking traffic.
The WiFi Pineapple is an easy-to-use device that would allow attackers to easily set up such attacks. When your laptop attempts to automatically connect to a network it remembers, the WiFi Pineapple watches for these requests and responds “Yes, that’s me, connect!”. The device is then built with a variety of man-in-the-middle and other attacks it can easily perform.
Someone clever could set up such a compromised hotspot in an area with high-value targets — for example, in a city’s financial district or anywhere people log in to do their banking — and attempt to harvest this personal data. It’s probably uncommon in the real world, but is very possible.
Protecting Yourself: Don’t do online banking or access sensitive data on public Wi-Fi if possible, even if the sites are encrypted with HTTPS. A VPN connection would likely protect you, so it’s a worthy investment if you find yourself regularly using public Wi-Fi.
If you use public Wi-Fi connections regularly, you may want to invest in a VPN. As a bonus, a VPN will allow you to bypass any filtering and website-blocking in place on the public Wi-Fi network, allowing you to browse whatever you want.
- Status
- Not open for further replies.
Similar threads
- Replies
- 3
- Views
- 457
- Replies
- 48
- Views
- 2K
- Replies
- 7
- Views
- 638
- Replies
- 0
- Views
- 302
- Replies
- 1
- Views
- 358
Share: